By Ryan Vogt on January 20, 2015
Just to expand on today’s brief discussion of the rather circular nature of government support for cryptographic software (and to a lesser extent, new technology in general):
- 1976: After the NBS (National Bureau of Standards) consulted with the NSA, the NSA made a slight modification to the forthcoming DES standard. For years there was significant academic suspicion that the NSA had weakened DES; in fact, they had strengthened it against an attack called “differential cryptanalysis” — a technique that wouldn’t be widely known in academic circles until the late 1980s.
- 1976: The Arms Export Control Act of 1976 is passed, making exporting cryptography that’s too good, as it were, equivalent to exporting munitions.
- 1991: Phil Zimmermann published online and for free PGP, a cryptosystem used to encrypt email (ensuring both privacy and lack of tampering). This would lead to a three-year criminal investigation against him under the 1976 Act.
- 1993: The Clipper chip was announced by the NSA. It would use what is — to the best of my knowledge — a secure cipher (Skipjack) to encrypt voice communications. However, there was a built-in backdoor in Clipper that allowed Skipjack to be “bypassed”, allowing for monitoring of seemingly secure voice communications. The project was abandoned by 1996.
- 1996: NIST (the National Institute of Standards and Technology) begins a massive search for a new cipher to standardize on (competition style!), to replace the aging and increasingly insecure DES. In 2001, Rijndael was announced as the new standard and named AES. To this day, it remains one of the most thoroughly tested and widely used ciphers, and is believed to be secure.
- 2007: NIST begins another competition to replace the now insecure SHA-1 hash, as well as the seemingly secure (but worryingly similar-in-design to SHA-1) SHA-2 family of hashes with a new standard. After a similar intensive search, Keccak was chosen. A few minor variations were made to Keccak to make it more flexible (nothing sinister). The revised version is expected to be named as SHA-3 pretty much any day now.
- Which brings us to now, and our talk today in class.
Back and forth, eh? And I’m sure there are lots more examples of help it / destroy it / help it / destroy it when it comes to cryptography!
Cheers
Read More | No Comments
By Jon Festinger on January 18, 2015
A concept well worth reflecting on: when is “free” not neutral? This article goes through the ins and outs of what it really means when carriers exempt certain apps from data charges, and not others. What do “net neutrality” rules have to look like to be meaningful and not a commercially manipulative sham? Read more here: Less than Zero — Backchannel — Medium.
jon
Read More | 2 Comments
By Ryan Vogt on January 18, 2015
Hello,
My name is Ryan, and I’m taking the first “student-hour” of the semester (feel free to bring fruit to throw). The topic is going to be: Open Source Licensing and Other Examples of Open Source.
There’s just one reading: Jacobsen v Katzer. Sorry about getting it out so close to Tuesday’s class, but it’s incredibly short (16 sparsely formatted pages).
An example of discussion questions to ponder (and please feel to bring your own questions as well, if something piques your interest or curiosity):
- Why would people want to open-source a project (e.g., software)? Why would they want to keep it proprietary?
- What sort of conditions, if any, would you want to put on the use of an (i.e., your) open-source project?
- Do such conditions foster or limit digital creativity?
- What does Jacobsen v Katzer tell us about the role of contract versus the role of copyright to open source? Do you agree or disagree?
- What other sort of non-software projects might you call open-source?
Cheers!
Read More | No Comments
By Jon Festinger on January 18, 2015

How is this for disturbing – hardly the percentage difference between “free” and “not free” countries you might wish for:
“Some 75 percent of respondents in countries classified as “free,” 84 percent in “partly free” countries, and 80 percent in countries that were “not free” said that they were “very” or “somewhat” worried about government surveillance in their countries.”
via Writers Say They Feel Censored by Surveillance – NYTimes.com
jon
Read More | No Comments
By Jon Festinger on January 13, 2015
In all their glory 😉

Read More | No Comments
By Jon Festinger on January 11, 2015
Please read the following in preparation for a class collaborative effort this Tuesday where we begin to imagine a “Charter of Digital Rights”: Internet Under Fire Gets New Manifesto — Backchannel — Medium.
jon
Read More | No Comments
By Jon Festinger on January 4, 2015
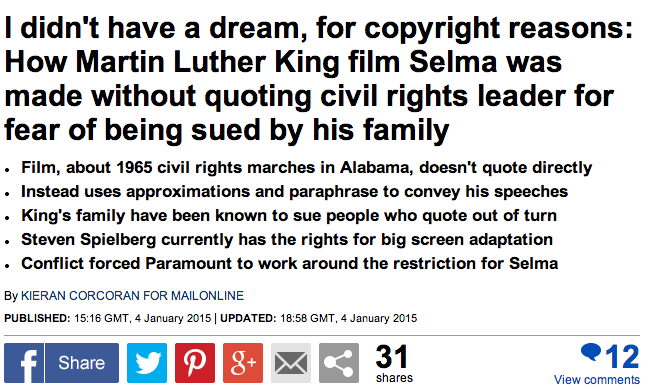
How Martin Luther King film Selma was made without quoting civil rights leader | Daily Mail Online.
This article will be among the topics for our first class. Issues of note:
1. Why didn’t Paramount sue for a declaratory judgment?
2. Does Hollywood have a vested interest in not strengthening the fair use exception to U.S. copyright law?
3. Does this simply prove that “Copyright chill” is real as you can’t have it both ways with respect to point 2 above.
4. Would the situation be different in Canada because fair dealing is different from fair use?
5. Would “moral rights” which is part of our law, change the situation if it had happened in Canada?
6. Implications of any/all of the above?
jon
Read More | No Comments












 Check out the UBC Video Game Law Course
Check out the UBC Video Game Law Course